Role Based Access Control¶
Note
Observe’s RBAC v2 feature is currently in Public Preview (PuPr). Please open a support request to have this feature enabled in your tenant. If you were using RBACv1 the documentation is still available here: RBAC v1 Intro
Role-Based Access Control (RBAC) allows you to control access to Observe actions and objects, based on the assigned group(s) in your organization. You can add users to groups with specific permissions within your Observe instance. Observe RBAC v2 provides the ability to grant access to specific objects, such as a particular dashboard, dataset, datastream, worksheet, etc. as well as grant the ability to perform certain actions, such as inviting users, creating worksheets, creating monitors, etc. Granting access to specific objects is done at the user and group level, and granting actions happens only at the group level.
Workspace Permissions¶
Tip
Any group that has been granted the Admin permission has access to all objects in the workspace.
Every Observe customer has a workspace which contains all of their users, data and objects (datastreams, datasets, monitors, worksheets, dashboards, etc) in it. By default, a new Observe tenant grants “edit” access to everything for the everyone group. In RBAC v2, you can now set a workspace-level policy that sets the default permissions of all newly created objects in your workspace, except for datasets and monitors. Navigate to Workspace Settings > Permissions to view and modify this setting. The default workspace permissions settings for RBACv2 are as follows:
Creator can Edit All types- The user creating the object will have edit access by default. This is the only immutable default sharing policy.Everyone can Edit All types- All active users in the workspace can view all objects by default.
You can customize workspace permissions to suit your organizations access control needs. The only immutable setting is Creator can Edit All types. Workspace permissions support either view or edit for all object types, or you can select one or all of the following targeted object types; Dashboard, Datastream and Worksheet.
In the following example, the creator of the object can edit anything they have created, all users in the viewer group can view all newly created dashboards by default, but nothing else. All users in the writer group can edit all newly created dashboards and worksheets, but nothing else. For securing access to existing content, we recommend using the permission manager
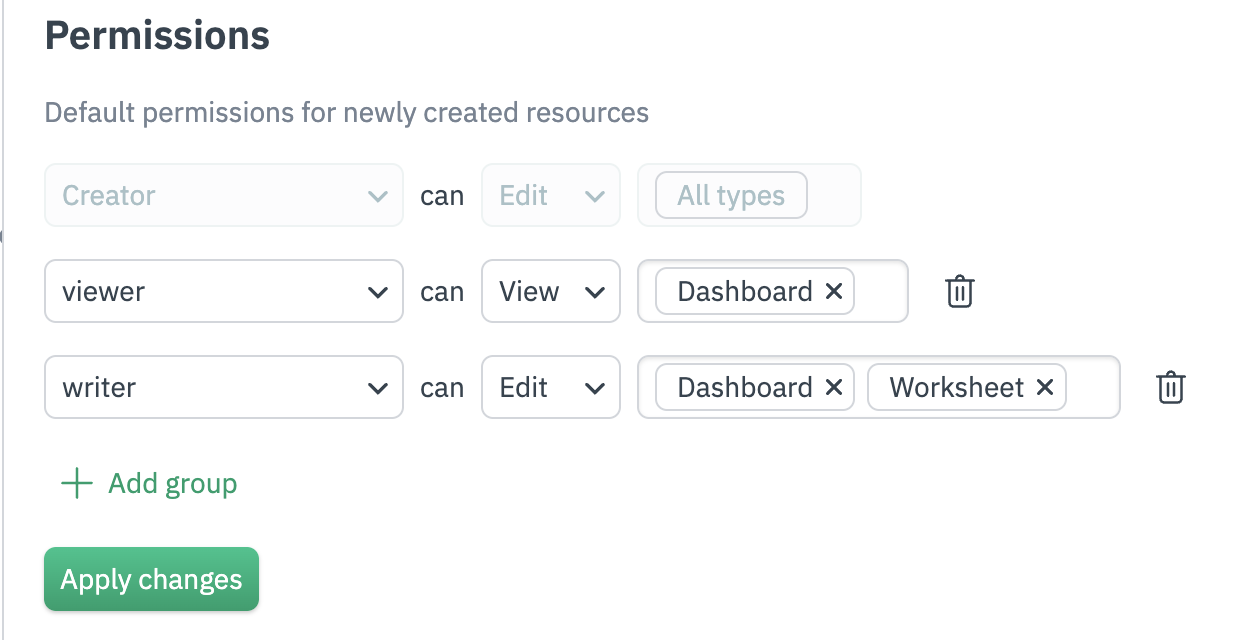
Figure 1 - Creating Custom Workspace Permissions
You can set up to 10 individual default workspace permissions. These permissions are not retroactive, and apply to objects created after you save your settings. All object-specific permissions can be changed at any time by users with Edit access to that particular object.
Default workspace permissions can be managed via the Observe Terraform provider, via the observe_workspace_default_grants resource.
RBAC Best Practices¶
When you grant permissions using RBAC, Observe recommends that you grant only the permissions required to perform a task. You do this by defining the actions taken on specific resources (objects) under specific conditions, also known as least-privilege permissions. You might start broad, while you explore the specific permissions required for your workload or use case. As your use case matures, you can work to reduce the permissions that you grant to work toward least privilege.
Permissions to perform specific actions are granted at the group level, see the section Group Permissions for more details. This includes operations like creating datasets, datastreams, worksheets, inviting users, etc.
Permissions to view or edit a specific instance of an object, such as a particular monitor, dashboard, dataset, etc. can be granted at the user or group level. There are two object-level level permissions; view and edit, you can also remove groups or users from being able to access the object at all. You can access these controls via the “share” arrow in the top right of the specific object’s page.
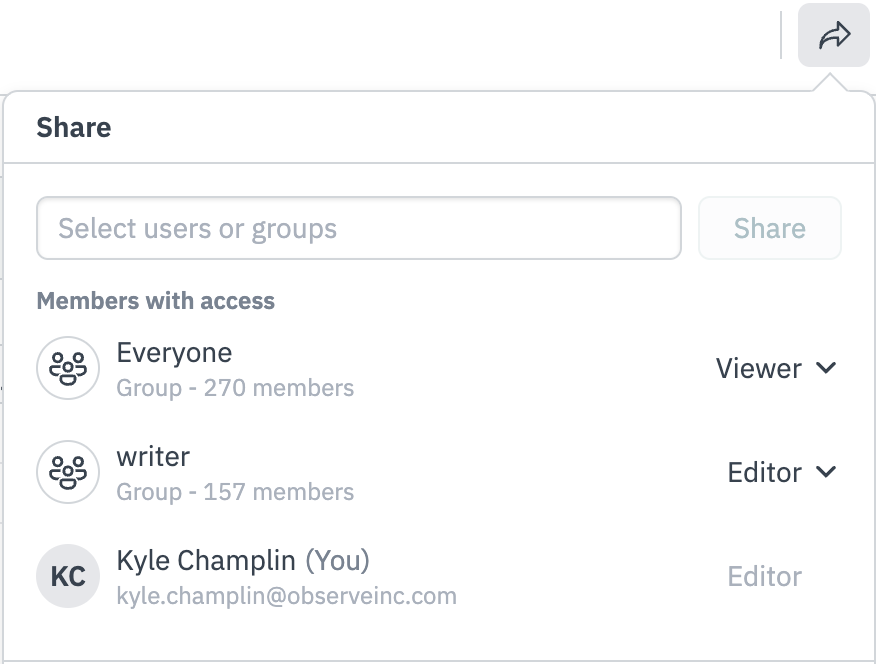
Figure 2 - Sharing Management Menu
Dataset Permissions¶
Similar to other object types, Dataset permissions are independent of each other, and there is no inheritance from parent dataset(s) to child dataset. Permissions for datasets are created during the publish process. When you go to publish a new dataset you are prompted to specify permissions. The Observe UI will provide a suggested intersection of all “input” (parent) datasets as a default option for permissions, however these suggestions can be changed by the publisher, allowing you to add or remove users and groups. If you use Terraform to manage your datasets, Observe also provides the observe_grant resource type to apply access controls to your dataset. If no access control policy is specified during dataset creation, Workspace Permissions will be applied.
Built-In Groups¶
Observe provides two default groups out of the box: Everyone and Admin. Both are reserved groups with special properties. The Everyone group includes all users in your Observe tenant; its membership is dynamic and cannot be changed. The Admin group can perform all actions and access everything in the account, and its permissions cannot be modified. These groups ensure consistent access and management across your Observe tenant. You cannot delete these groups.
Group Permissions¶
Groups are subject to the following permissions, note that the Admin permission provides administrative access to the entire tenant workspace and include actions not explicitly listed in the Set permissions table.
Object |
Permission |
Description |
|---|---|---|
Worksheets |
Create |
Create new Worksheets |
Datasets |
Create |
Create and publish new Datasets |
Datastreams |
Create |
Create new Datastreams and associated ingestion tokens, pollers and filedrop configs |
Monitors |
Create |
Create new monitors and actions |
Monitors |
Mute |
Mute existing monitors and alerts |
Dashboards |
Create |
Create new Dashboards |
Dashboards |
Export |
Create new Dashboard Report |
Authtokens |
Create |
Create auth tokens for use with the Observe REST API |
Users |
Invite |
Invite and reactivate users |
Users |
Delete |
Delete and deactivate users |
Permission Manager¶
Note
Permission manager is currently in private preview, please open a support ticket via your support portal to have this enabled in your tenant.
Permission manager is located in the Account settings page of your Observe tenant. Permission manager allows you to quickly apply access permissions for multiple Datasets, Dashboards, Monitors and Worksheets. For all object types, you can filter by group and associated group permissions.
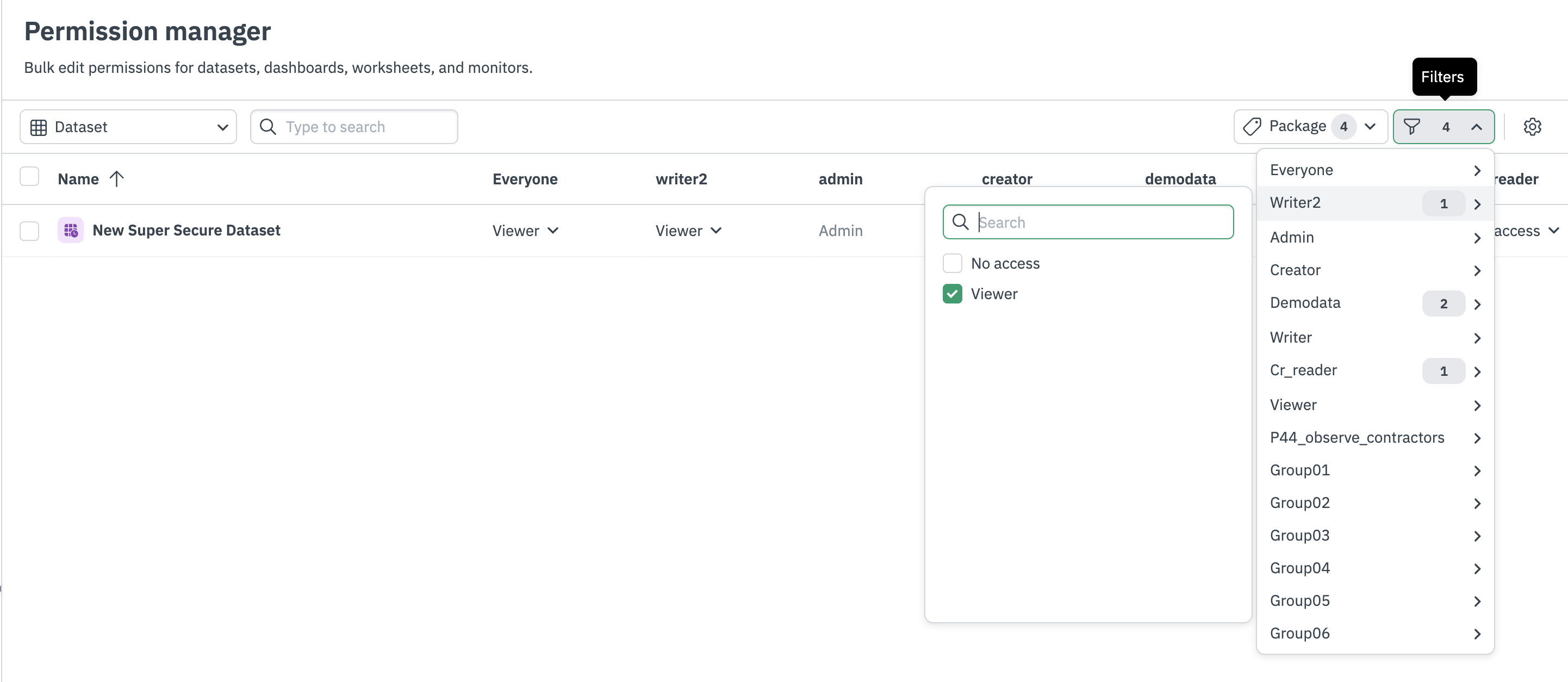
Figure 3 - Filter by group permissions
For datasets, permission manager allows you to filter by package name.
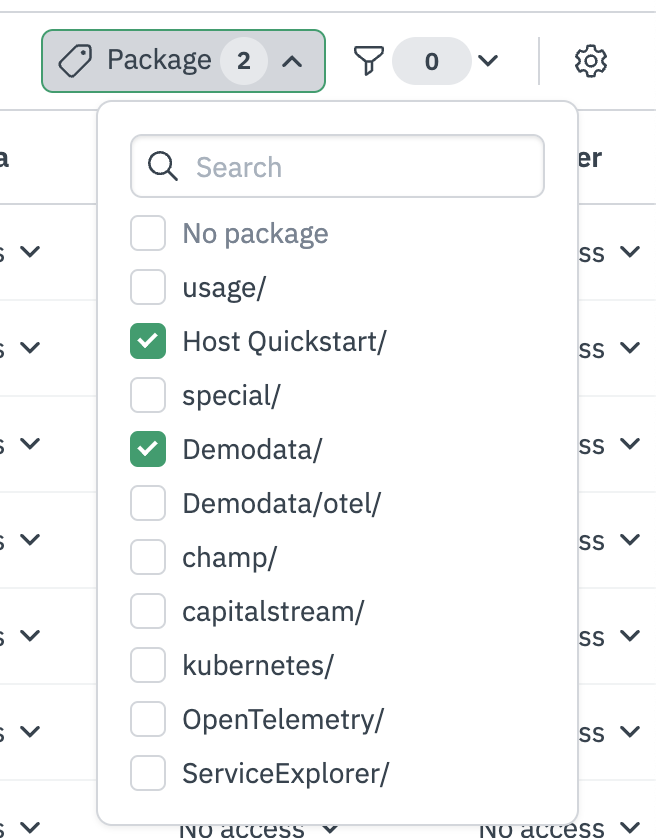
Figure 4 - Filter by dataset package
Making bulk permission changes¶
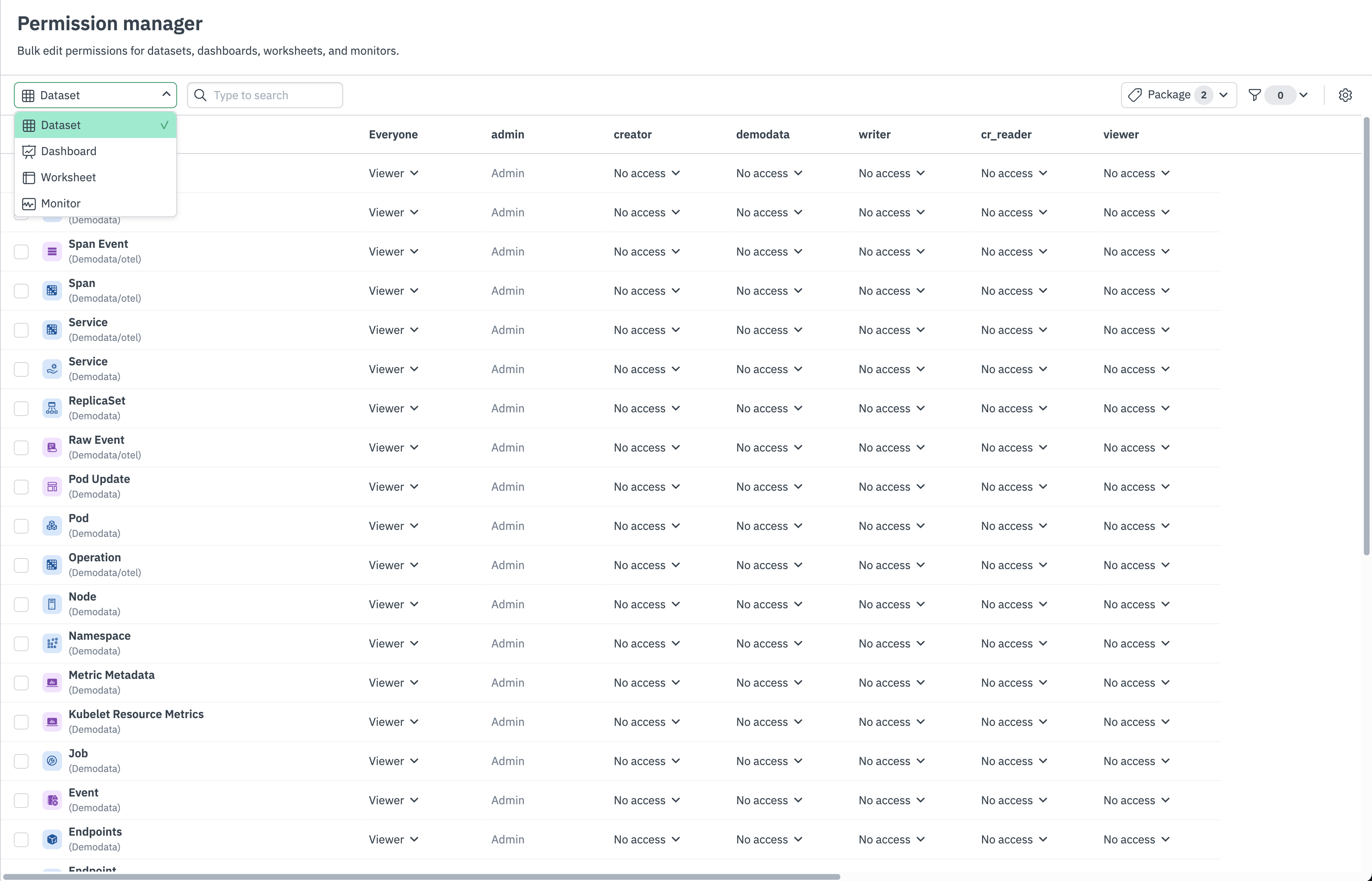
Figure 5 - Permission Manager
To change the RBAC grants for multiple objects at one, select one or many objects via the left-most column, and then click the Edit permissions button. This will open a modal that provides three options:
Replace- This will completely replace any existing permissions for the selected objects with new permissions you specify in the next step.Add- This will add permissions in addition to any existing permissions to the selected objects. You will specify the additional permissions in the next step.Remove- This will remove permissions that you select in the next step.
Next, specify which permissions to replace, add or remove. The permissions that are initially listed are an intersection of the current permissions of the selected objects. Select Review updates to review your changes. Permission manager provides a “diff”-style view of your changed permissions when you select View all changed permissions. Finally, select Yes, update to apply your new permissions.
Making single object changes¶
You can also directly edit access at an individual group and object level. Hover over any cell in the Permission manager table, and select Viewer, Editor or Remove to set permissions for that group and object.
RBAC and SAML SSO¶
Observe supports integration with an external Identity Provider (IdP) via the SAML protocol. For integration specific instructions, see the documentation at Single Sign On (SSO) Configurations for Observe. If you wish to automatically add users to an Observe group, based on their SAML group membership, you must create a group in Observe that matches the group name in the SAML assertion.