Set default permissions using RBAC
Role-Based Access Control (RBAC) allows you to control access to Observe actions and objects, based on the assigned group(s) in your organization. You can add users to groups with specific permissions within your Observe instance. Observe RBAC v2 provides the ability to grant access to specific objects, such as a particular dashboard, dataset, datastream, worksheet, etc. as well as grant the ability to perform certain actions, such as inviting users, creating worksheets, creating monitors, etc. Granting access to specific objects is done at the user and group level, and granting actions happens only at the group level.
Workspace permissions
TipAny group that has been granted the Admin permission has access to all objects in the workspace.
Every Observe customer has a workspace containing all of their users, data and objects, such as Datastreams, Datasets, monitors, Worksheets, and dashboards. By default, a new Observe tenant grants “edit” access to everything for the everyone group. In RBAC v2, you can now set a workspace-level policy that sets the default permissions of all newly created objects in your workspace, except for datasets and monitors. From the left navigation rail, select Your username > Manage account > Permission manager to view and modify this setting. The default workspace permissions settings for RBACv2 are as follows:
- Creator can Edit All types - The user creating the object will have edit access by default. This is the only immutable default sharing policy.
- Everyone can Edit All types - All active users in the workspace can view all objects by default.
You can customize workspace permissions to suit your organizations access control needs. The only immutable setting is Creator can Edit All types. Workspace permissions support either view or edit for all object types, or you can select one or all of the following targeted object types; Dashboard, Datastream and Worksheet.
In the following example, the creator of the object can edit anything they have created, all users in the viewer group can view all newly created dashboards by default, but nothing else. All users in the writer group can edit all newly created dashboards and worksheets, but nothing else.
To secure access to existing content, use the Permission manager.
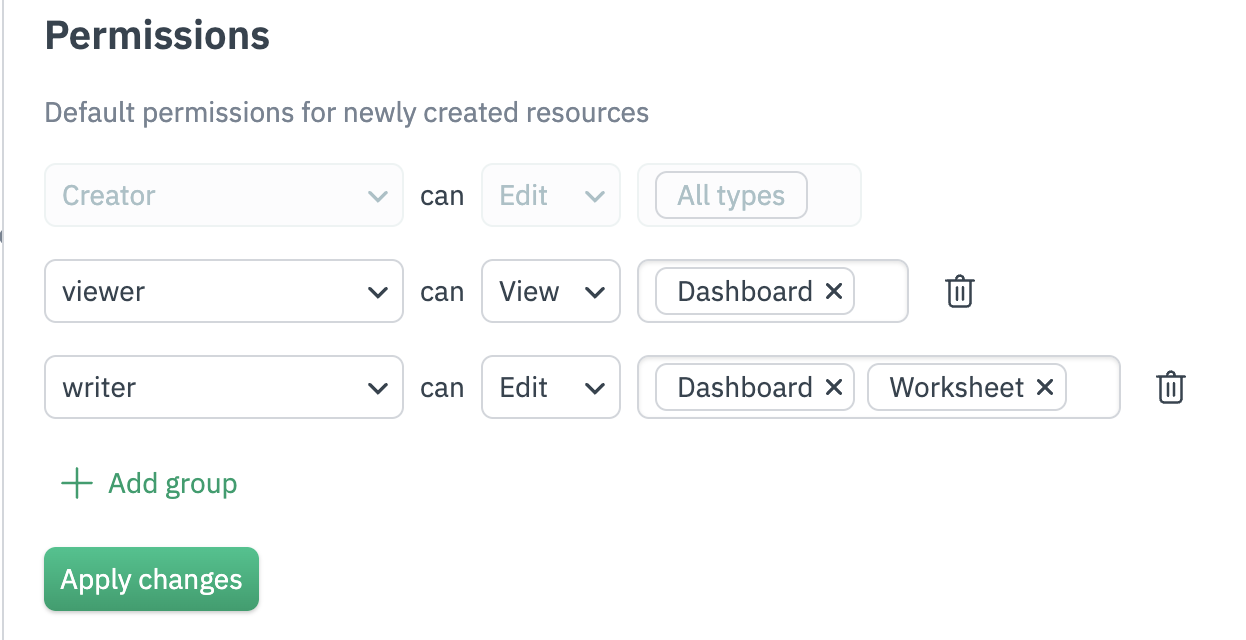
You can set up to 10 individual default workspace permissions. These permissions are not retroactive, and apply to objects created after you save your settings. All object-specific permissions can be changed at any time by users with Edit access to that particular object.
Default workspace permissions can be managed via the Observe Terraform provider, via the observe_workspace_default_grants resource.
RBAC best practices
When you grant permissions using RBAC, Observe recommends that you grant only the permissions required to perform a task. You do this by defining the actions taken on specific resources (objects) under specific conditions, also known as least-privilege permissions. You might start broad, while you explore the specific permissions required for your workload or use case. As your use case matures, you can work to reduce the permissions that you grant to work toward least privilege.
Permissions to perform specific actions are granted at the group level, see the section Group Permissions for more details. This includes operations like creating datasets, datastreams, worksheets, inviting users, etc.
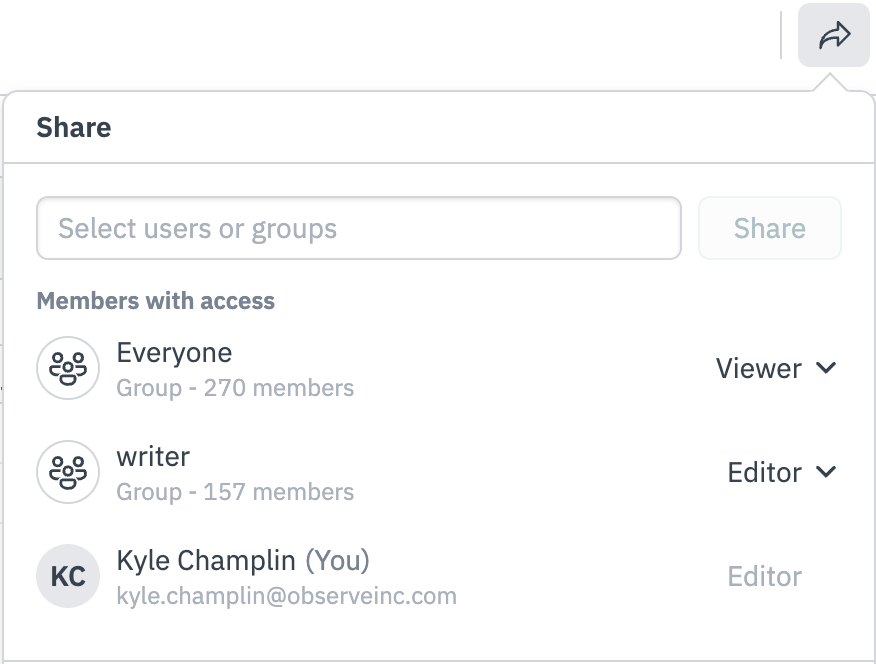
Permissions to view or edit a specific instance of an object, such as a particular monitor, dashboard, dataset, etc. can be granted at the user or group level. There are two object-level level permissions; view and edit, you can also remove groups or users from being able to access the object at all. You can access these controls via the “share” arrow in the top right of the specific object’s page.
Dataset permissions
Similar to other object types, Dataset permissions are independent of each other, and there is no inheritance from parent dataset(s) to child dataset. Permissions for datasets are created during the publish process. When you go to publish a new dataset you are prompted to specify permissions. The Observe UI will provide a suggested intersection of all “input” (parent) datasets as a default option for permissions, however these suggestions can be changed by the publisher, allowing you to add or remove users and groups. If you use Terraform to manage your datasets, Observe also provides the observe_grant resource type to apply access controls to your dataset. If no access control policy is specified during dataset creation, Workspace Permissions will be applied.
RBAC and SAML SSO
Observe supports integration with an external Identity Provider (IdP) via the SAML protocol. For integration specific instructions, see the documentation at Single Sign On (SSO) Configurations for Observe. If you wish to automatically add users to an Observe group, based on their SAML group membership, you must create a group in Observe that matches the group name in the SAML assertion.
See Single sign-on.
Updated 9 days ago